Cyber Security Frameworks Series
While Cyber Security Awareness Month may have concluded in October, it is a matter of fact that the importance of cyber security should remain an all-time, all-year-round, ongoing top priority for all organisations. In the ever-evolving landscape of cyber threats, protecting sensitive data, ensuring business continuity, and upholding stakeholder and client confidence all depend on taking a proactive approach and following established protocols and guidelines.
Cyber threats do not follow a schedule, and neither should our dedication to cyber security. It is now imperative for organisations to adopt comprehensive frameworks that offer a structured approach to managing and mitigating cyber risks.
In a previous post, we explored the Australian Cyber Security Centre’s (ACSC) Essential 8 Framework. Now, we continue our exploration of the National Institute of Standards and Technology (NIST)’s Cyber Security Framework (CSF), another important pillar in the field of cyber security.
About the National Institute of Standards and Technology (NIST) Cyber Security Framework (CSF)
In February 2013, the President of the United States issued Executive Order 13636, titled “Improving Critical Infrastructure Cyber security,” tasking NIST with creating the Cyber Security Framework. This voluntary guide, based on industry standards, enhances organisations’ management of cyber security risks and promotes communication among stakeholders.
The Framework is a dynamic, “living document” designed for continuous improvement. Regular updates incorporate industry feedback and lessons learned from practical implementation, ensuring its relevance in the ever-evolving landscape of cyber security challenges, threats, and solutions.
An Introduction to the Components of the NIST Framework
There are three primary components to the Cyber security Framework: the Core, Implementation Tiers, and Profiles. Let’s explore each.
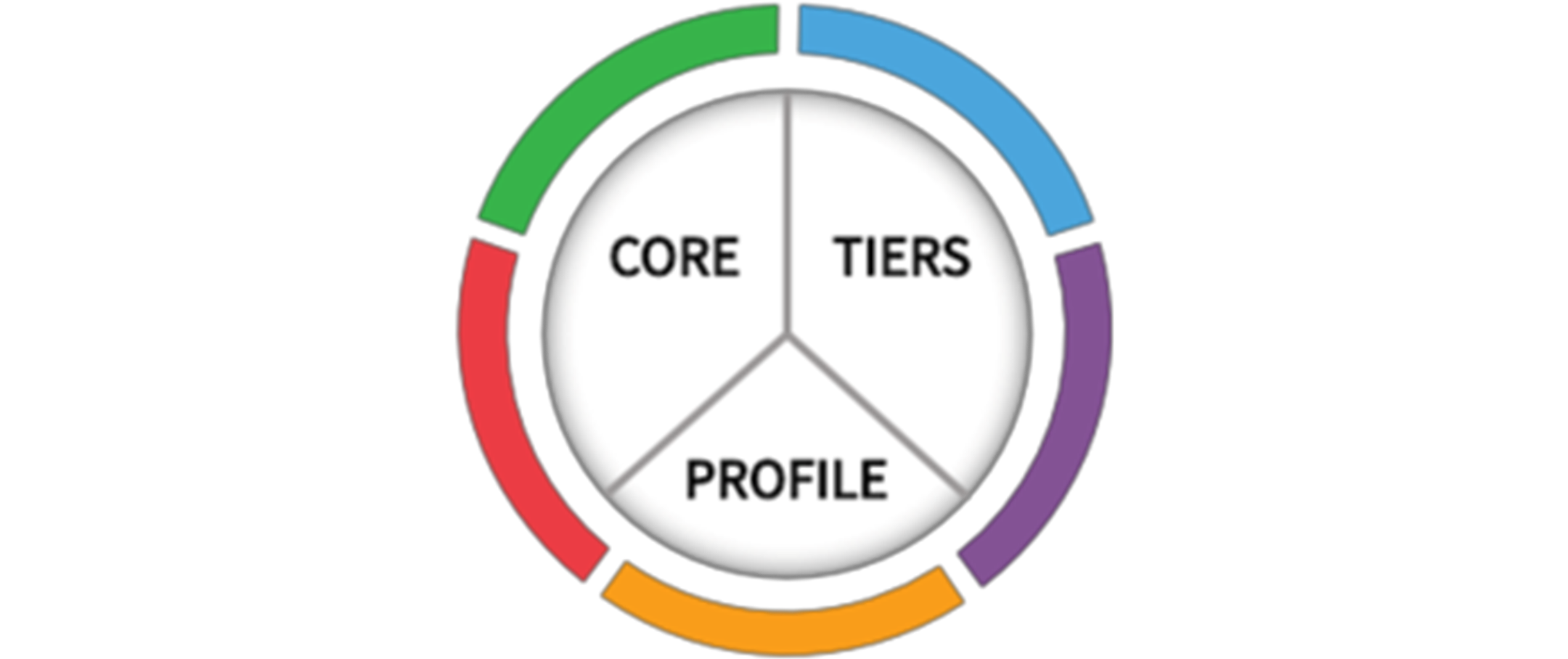
Image source: https://www.nist.gov/cyberframework/getting-started
1) The Core
The Framework Core serves as a user-friendly guide for organisations to manage cyber security risks effectively. Using a common language, it provides a set of desired activities and outcomes that align with existing cyber security and risk management processes. Designed to facilitate communication between teams, the Core includes three parts: Functions, Categories, and Subcategories.
The five high-level functions—Identify, Protect, Detect, Respond, and Recover—are applicable not only to cyber security risk management but also to risk management in general. Within these functions, 23 Categories are further divided, aligning with the Framework’s structure.
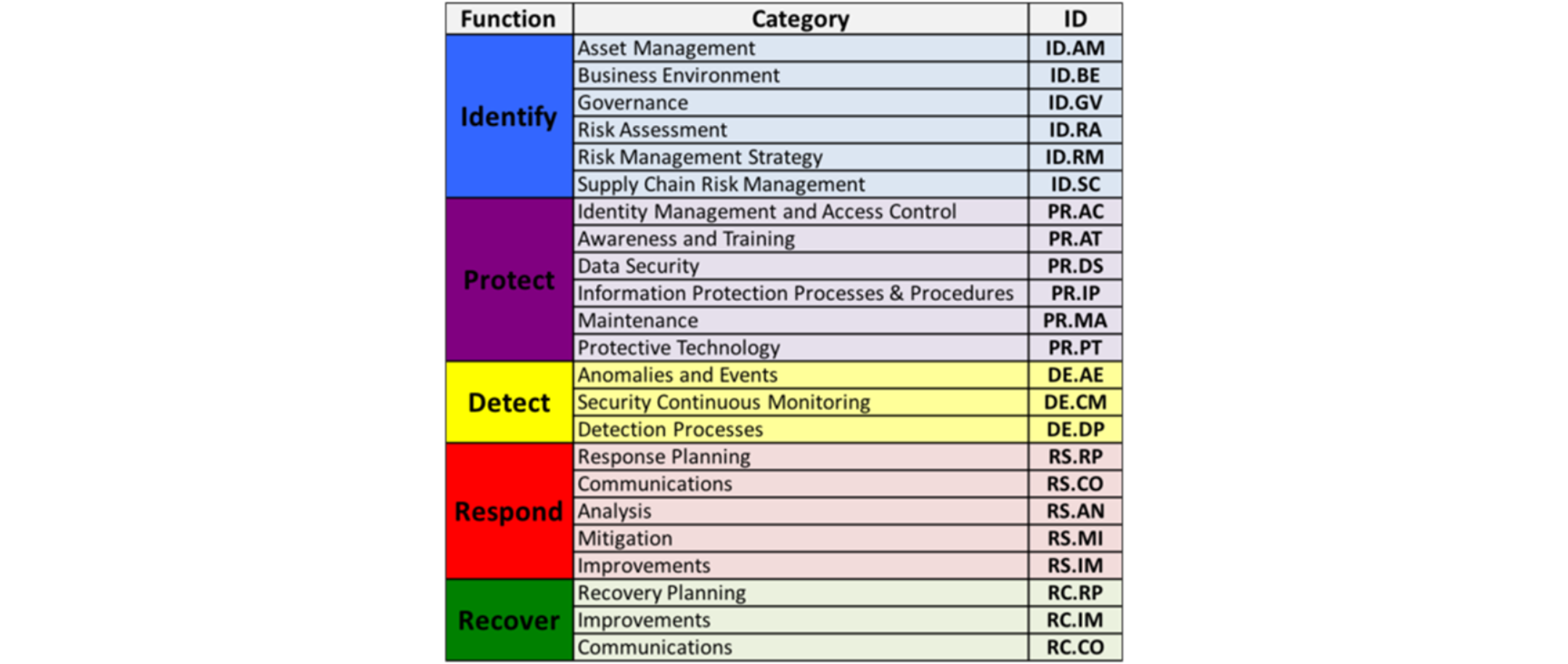
Image source: https://www.nist.gov/cyberframework/online-learning/cybersecurity-framework-components
Categories within the Framework address a broad spectrum of cyber security objectives for organisations, spanning cyber, physical, and personnel domains, emphasising tangible business outcomes. Going deeper, the 108 Subcategories represent outcome-driven statements, guiding the creation or enhancement of a cyber security program.
The Framework’s outcome-driven approach allows organisations flexibility in implementing risk-based solutions tailored to their specific needs, without prescribing specific methods for achieving these outcomes.
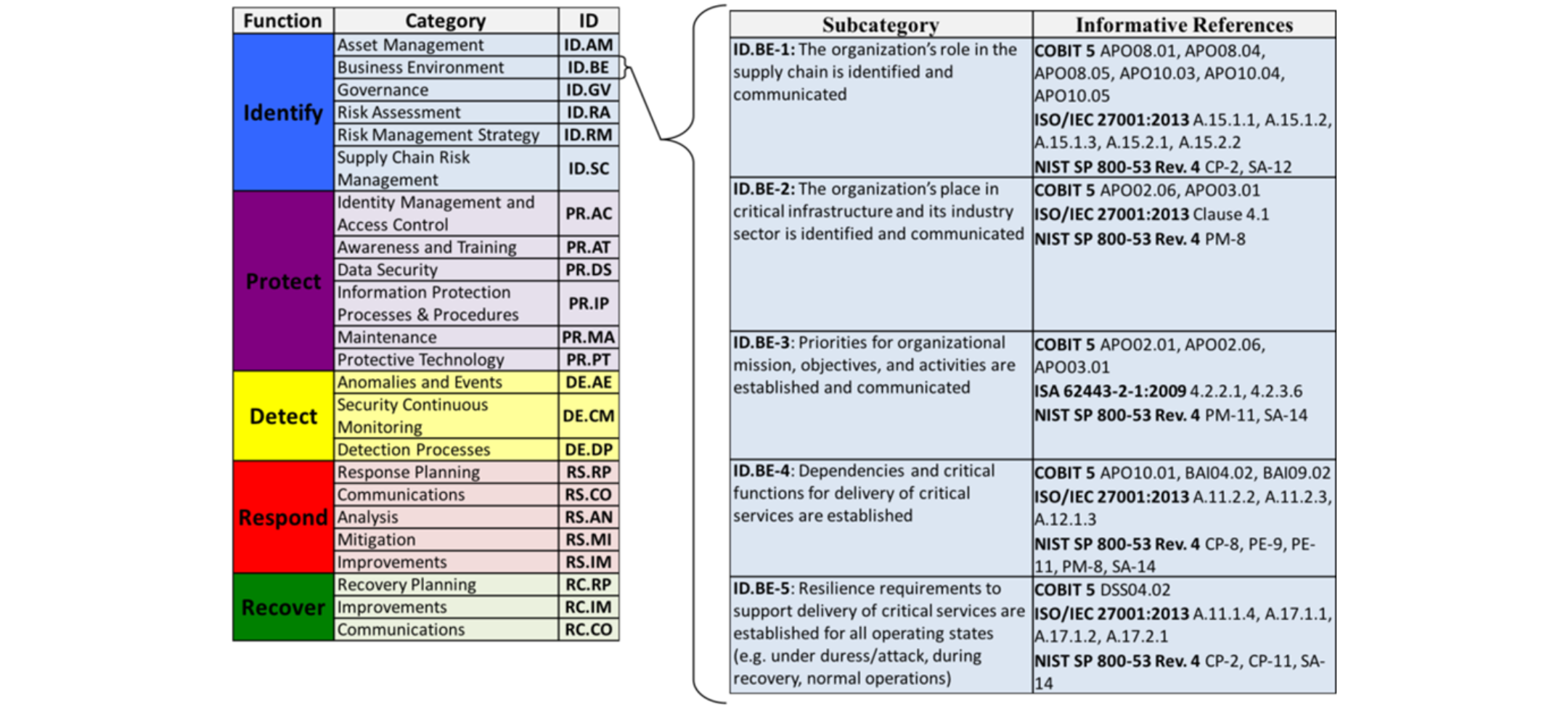
Image source: https://www.nist.gov/cyberframework/online-learning/cybersecurity-framework-components
The Business Environment Category (ID.BE) showcases five Subcategories as examples of outcome-focused statements within the Framework Core. These statements guide organisations in tailoring their cyber security programs. Informative References, listed in the adjacent column, offer technical support to the Core. Organisations have the flexibility to choose from these references, using them selectively or comprehensively to inform activities aligned with the desired outcomes outlined in each Subcategory.
2) The Tiers
The Framework Implementation Tiers serve as a vital tool for organisations, offering insight into how they approach cyber security risk management. Ranging from Partial (Tier 1) to Adaptive (Tier 4), these Tiers indicate the level of rigour in an organisation’s cyber security practices. They go beyond internal processes, shedding light on the integration of cyber security risk decisions into broader risk considerations.
Additionally, the Tiers reflect the organisation’s collaboration in sharing and receiving cyber security information with external parties. This nuanced understanding helps organisations tailor their cyber security programs based on factors such as risk appetite, mission priority, and budget, making the Tiers a valuable communication tool in the cyber security landscape
.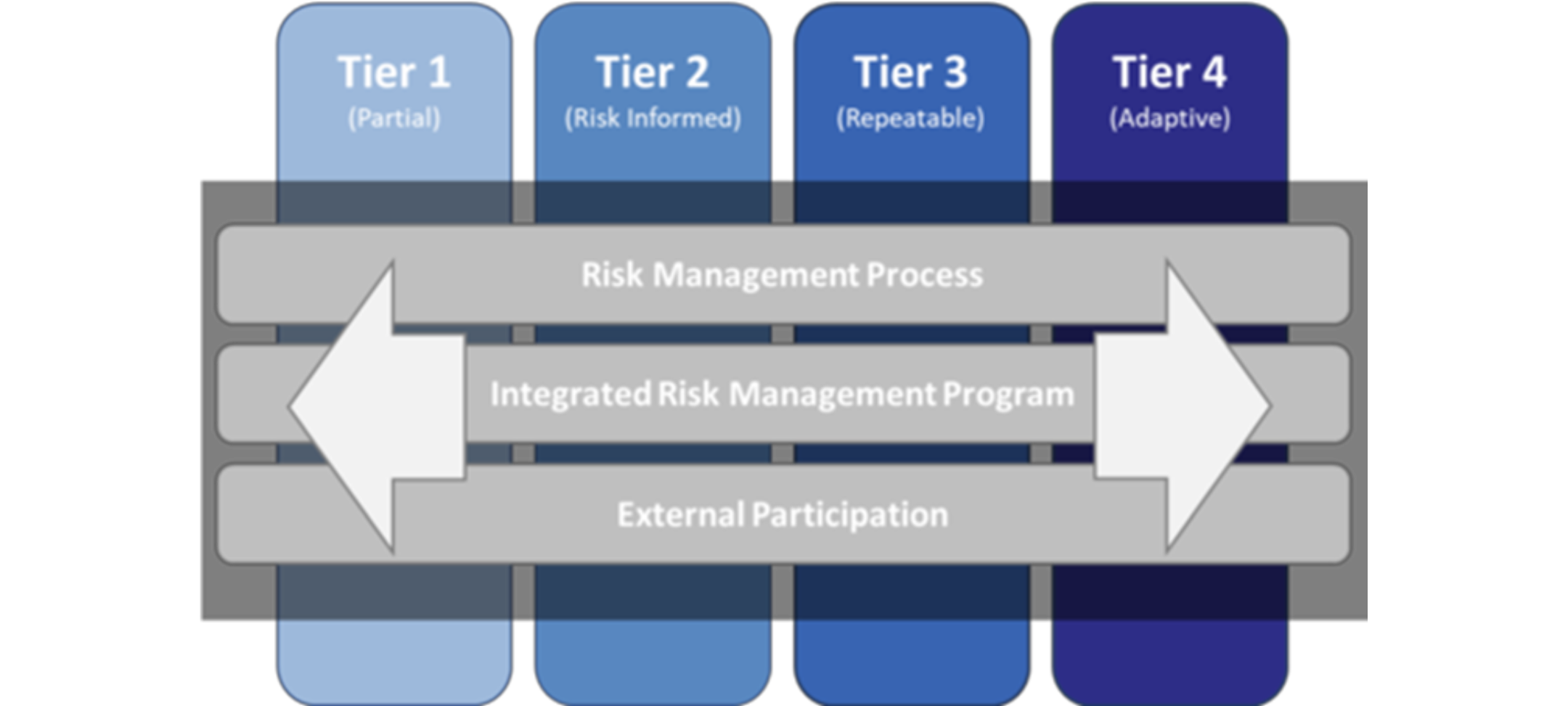
Image source: https://www.nist.gov/cyberframework/online-learning/cybersecurity-framework-components
When selecting a Framework Implementation Tier, organisations should align it with their goals, ensuring it effectively reduces cyber security risk to an acceptable level. It’s crucial to note that Tiers don’t necessarily reflect maturity levels. The chosen Tier should be both feasible and in line with organisational objectives, considering implementation feasibility, both fiscally and operationally.
2) The Profiles
The Framework Profiles is a personalised alignment of an organisation’s requirements, objectives, risk appetite, and resources with the desired outcomes of the Framework Core. These profiles serve as a valuable tool to identify and prioritise opportunities for enhancing cyber security within an organisation. By comparing a “Current” Profile with a “Target” Profile, organisations can effectively pinpoint areas for improvement, creating a roadmap to fortify their cyber security posture.

Image source: https://www.nist.gov/cyberframework/online-learning/cybersecurity-framework-components
Profiles optimise the voluntary Cyber Security Framework for organisational benefit. There’s no definitive ‘right’ or ‘wrong’ method. One approach involves mapping cyber security requirements, mission objectives, and practices against Framework Core subcategories, forming a Current-State Profile. This comparison illuminates gaps between organisational objectives and the current operating state, offering insights to refine cyber security strategies effectively.
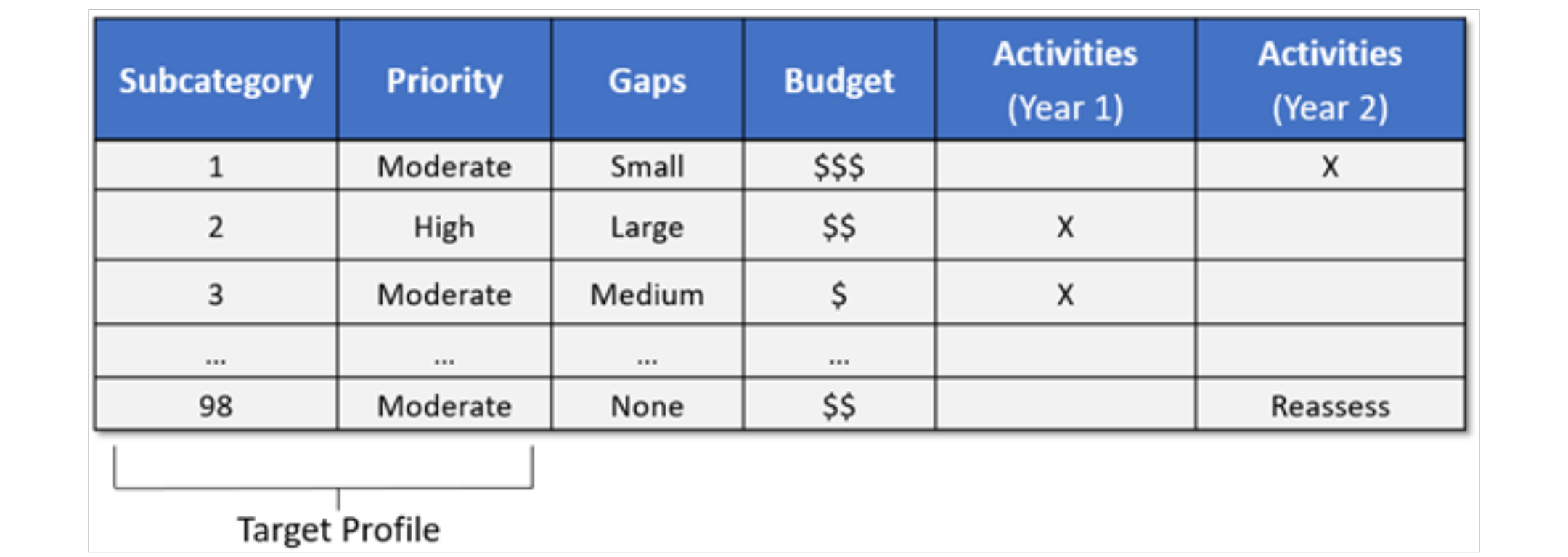
Image source: https://www.nist.gov/cyberframework/online-learning/cybersecurity-framework-components
Creating profiles and conducting gap analyses empower organisations to develop a prioritised implementation plan. By assessing the priority and size of gaps, and estimating corrective action costs, organisations gain valuable insights for planning and budgeting cyber security improvement activities.
Is the NIST Framework for you?
The Cyber Security Framework caters to organisations of varying sizes, sectors, and maturities, offering versatility beyond its initial Critical Infrastructure (CI) focus. Its built-in customisation mechanisms—Tiers, Profiles, and Core—enable adaptability for any organisation.
The Framework’s outcome-driven approach, devoid of rigid mandates, ensures scalability. Whether a small organisation with a limited cyber security budget or a large corporation with ample resources, each can approach cyber security outcomes in a manner feasible for them. This flexibility allows the Framework to be valuable for organisations at different stages, from those establishing a cyber security program to those with mature programs.
Applications and Advantages of the NIST Framework
Unified Risk Management Approach: The Framework establishes a standardised language and methodology for cyber security risk management, featuring a customisable Core adaptable to diverse organisational needs.
Synergy with Existing Systems: It complements and enhances existing cyber security programs and risk management processes, fostering a cohesive and comprehensive approach.
Guidance Across Organisational Levels: Serving as a comprehensive guide, the Framework aids decision-making at all organisational levels, from senior executives to business processes and implementation operations.
End-to-End Communication Facilitation: It facilitates seamless end-to-end risk management communications throughout the organisation, ensuring a unified and clear understanding.
Enhanced Processes with Profiles: Framework Profiles enhance and introduce organisational processes, promoting improved communication and effective collaboration.
Integrated Communication Tool: Paired with the Framework’s accessible language, Profiles become an integrated communication tool, ensuring effective communication within the organisation.
Utility Maximisation through Implementation Plans: Combining Profiles with implementation plans maximises the Framework’s utility, allowing for cost-effective prioritisation and communication of improvement activities to stakeholders, suppliers, and partners.
Demonstrable Due Care: The Framework and Profiles serve as robust artifacts for demonstrating due care in cyber security practices.
Insights and Communication via Implementation Tiers: Implementation Tiers offer valuable insights into an organisation’s cyber security risk management perspective, serving as a valuable communication tool for discussing mission priority, risk appetite, and budget considerations.
Conclusion
The NIST Framework is pivotal in cyber security, offering a standardised approach for effective risk management. It complements existing programs, guides decision-making, and enhances communication, showcasing its impact on organisational cyber security.
For more in-depth information about the NIST Cyber Security Framework, visit the National Institute of Standards and Technology’s official website.
At New Era Technology, we understand the critical importance of robust cyber security as the lifeline of your business.
Our commitment extends beyond mere understanding; we offer a comprehensive suite of cyber security solutions designed to fortify your organisation’s defences.
Embracing a holistic approach, we tailor our offerings to elevate your cyber security maturity level. Whether applying the E8 framework, the NIST framework, or an integrated solution that harmoniously combines both, our goal is to empower your organisation with resilient and adaptive cyber security measures.
Contact us today to discover more about the tailored solutions your business needs.
Information for this blog post was sourced from the National Institute of Standards and Technology.

 Canada
Canada LATAM
LATAM New Zealand
New Zealand UAE
UAE United Kingdom
United Kingdom United States
United States