Understanding Zero Trust and How It Works
Over recent years, Zero Trust has emerged as a strategic and holistic approach to cybersecurity. By eliminating implicit trust and verifying each access, this integrated solution covers users, applications, and infrastructure, regardless of their location or nature.
Gone are the limitations of product-centric approaches. With Zero Trust, your entire control ecosystem is protected, spanning network, identity management, cloud, applications, endpoints, and IoT devices. This proactive approach operates across all layers of your digital estate, continuously verifying transactions, asserting least privilege, and deploying advanced intelligence and real-time response to neutralise threats effectively.
With Zero Trust, you can confidently enforce policy-driven protection for your valuable assets, while treating every user and application as potential threats. Whether in a hybrid work environment or any location, Zero Trust adapts seamlessly and safeguards your people, data, applications, and devices.
However, it is important to understand that despite how some security vendors may market it, zero trust is not something you can buy off the shelf. After all, it is a strategic framework that requires a systematic approach for implementation.
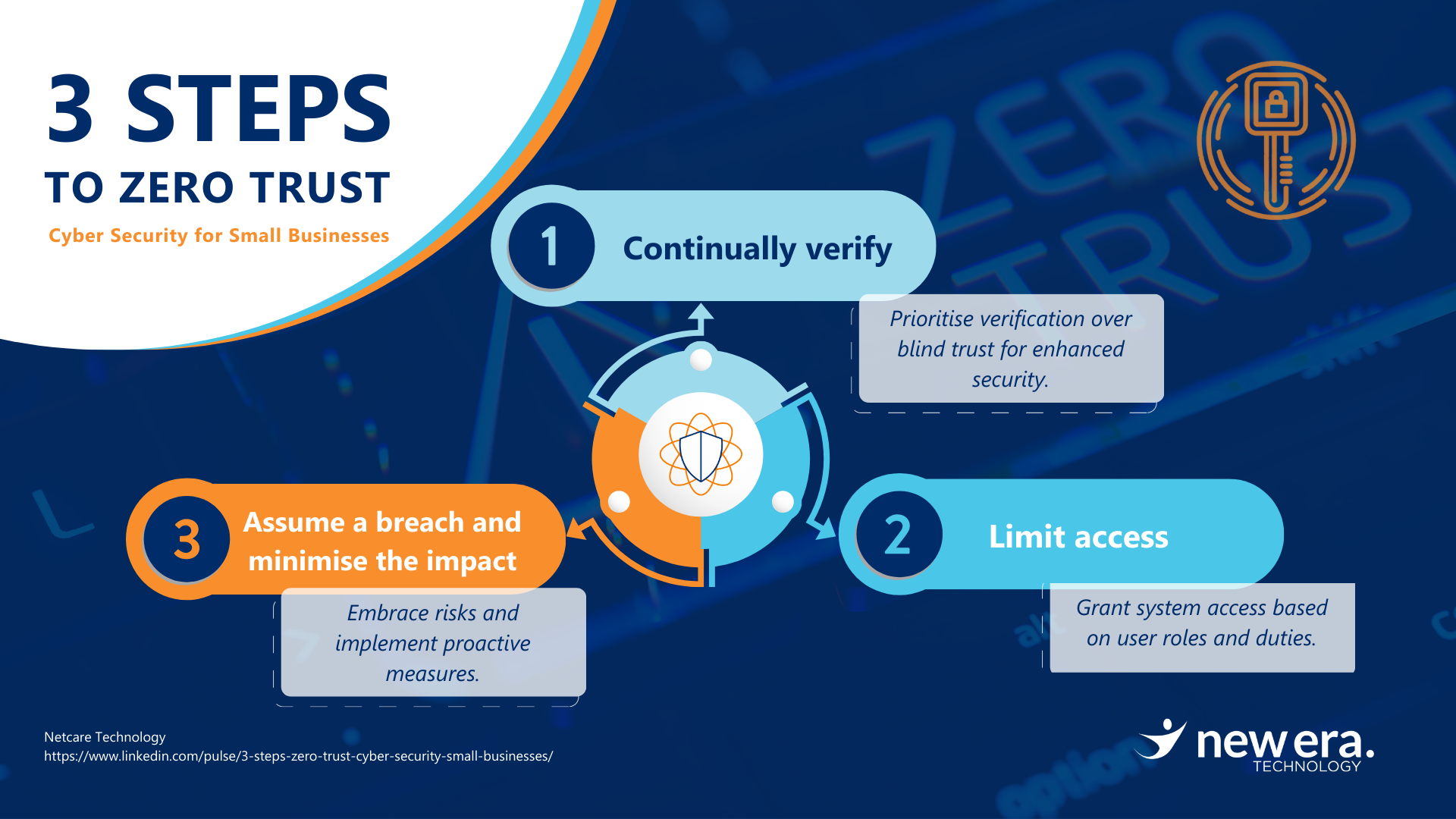
3 Steps to Adopting Zero Trust Framework
Zero Trust is a comprehensive outlook that ensures a robust shield for your organisation against ever-evolving threats by observing the following 3 core principles that you need to implement:
Step 1: Continually Verify
Aim to adopt a security approach of “never trust, always verify” by consistently validating the identity and access rights of users, devices, and applications. Strong identity and access (IAM) controls can play a vital role in achieving this objective. These controls enable you to define roles and access privileges, guaranteeing that only authorised users gain access to the appropriate information.
Step 2: Limit Access
Cyberattacks often result from the misuse of privileged access, making it essential to restrict such access to the minimum necessary for daily operations. Organisations have adopted various security practices to achieve this goal:
- Just-in-time access (JIT): Users, devices, or applications are granted access for a specific timeframe, limiting their exposure to critical systems and reducing potential risks.
- Principle of least privilege (PoLP): Users, devices, or applications receive only the minimum access or permissions required to carry out their specific job responsibilities.
- Segmented application access (SAA): Users are restricted to accessing only approved applications, effectively preventing malicious actors from infiltrating the network.
Step 3: Assume Breach and Minimise the Impact
Take a proactive stance in bolstering your cybersecurity by assuming the presence of risk. This approach entails considering applications, services, identities, and both internal and external networks as potentially compromised from the start. By doing so, you’ll boost your ability to respond swiftly to any breaches, reduce the impact of incidents, enhance your overall security measures, and, above all, safeguard your business effectively. Don’t wait for threats to strike; assume risk and stay ahead in protecting your valuable assets.
he feasibility of implementing these principles may differ for each organisation, influenced by its individual security requirements, capabilities, and challenges. In essence, the journey towards achieving Zero Trust is custom-tailored to suit the distinct needs and characteristics of your business.
New Era Technology is here to help.
Elevate your business to new heights with an expert IT Service Provider like New Era Technology — offering a comprehensive range of solutions and services, complete with advanced resources and tools, to combat threats, so you can confidently focus on your core business, knowing that your IT security is in capable hands.
Partner with New Era and unlock the true potential of your business.

 Canada
Canada LATAM
LATAM New Zealand
New Zealand UAE
UAE United Kingdom
United Kingdom United States
United States