The ‘end-user’ layer of network security may be your organisation’s biggest vulnerability.
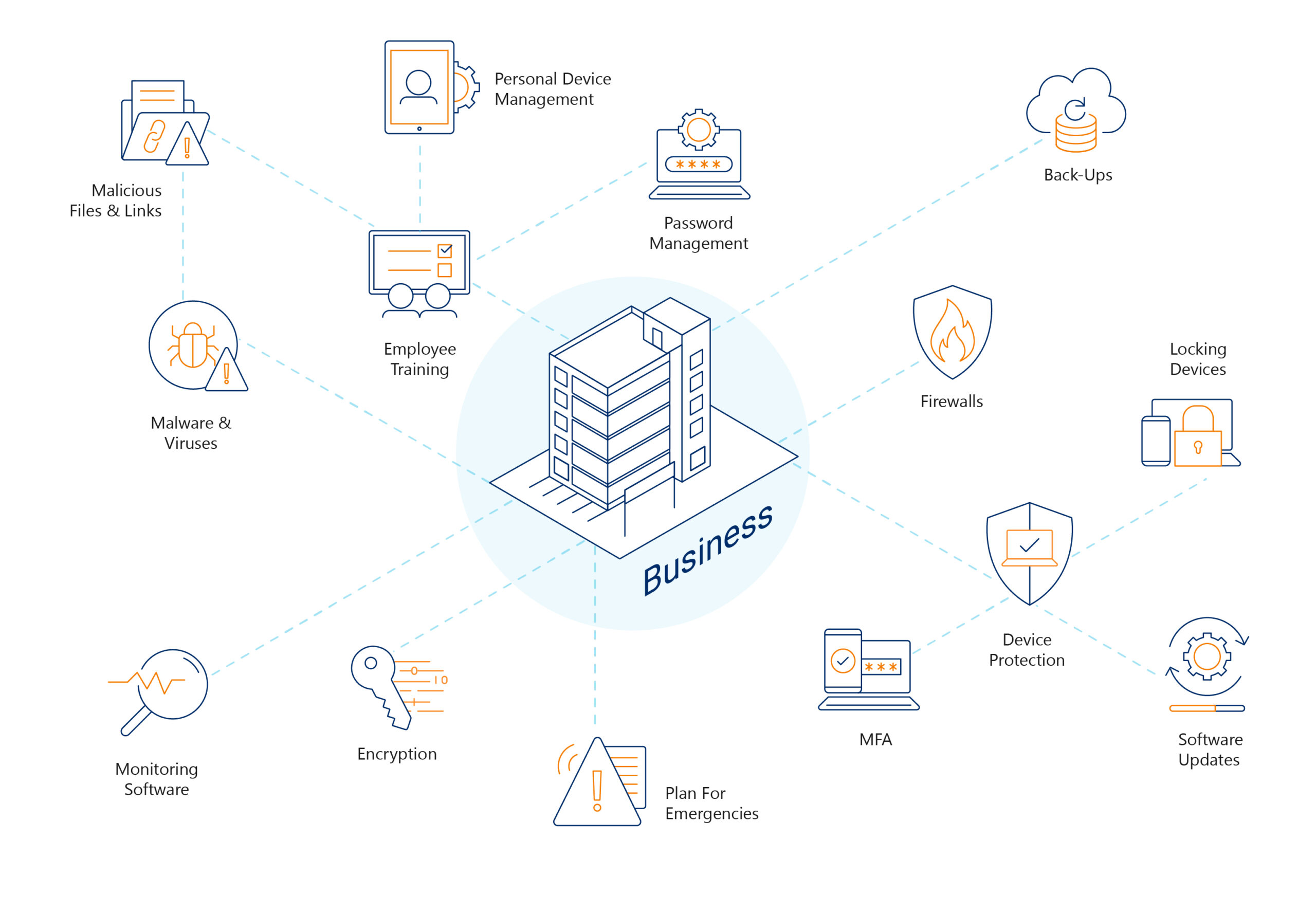
There are multiple points of vulnerability for security breaches within businesses’ IT networks. Everything from routers and firewalls, to servers, to the devices used by staff every day represents a point of potential risk. The employee’s role in maintaining a secure digital environment is one aspect of security that is often overlooked.
Of course, the essential security elements are important such as firewalls and anti-virus software. However, it is the next layer of security where organisations can make simple adjustments to their policies to reduce their risk of attack, loss of data and reputation damage.
Everyone plays a role in cyber security
All levels of staff play a role in maintaining security, and employees must know their role in reducing risk. Employees must be aware of identifying risks and mitigating them where possible.
Simple steps you can take to improve your security
There are some easy actions your business can take to equip your team with the knowledge to help protect your data as much as possible and minimise any potential disruption to productivity and delivering services to clients.
Password management
Employees likely have many online accounts they use for all sorts of purposes, and they may often use the same or similar passwords to make it easier to remember. The downside to this is that it is also much easier for hackers to gain access to multiple accounts using one set of credentials. Passwords should always be unique for every employee’s different accounts, to reduce the risk of a breach via stolen credentials. In particular, their work accounts should not share any passwords with any personal accounts.
Multi-Factor Authentication
Another way of reducing risk and ensuring compliance is to enable Multi-Factor Authentication (MFA), also known as Two-Factor Authentication (2FA).
Multi-Factor Authentication (MFA) is one of the Essential Eight and is recommended by ACSC as one of the core eight components of security. Read more about the Essential Eight.
MFA helps protect businesses by providing an additional layer of security for passwords. Users will be required to authenticate their login via a second method such as a generated code sent via email, SMS, or an alert prompt sent to an app on your mobile device.
Encourage the locking of devices
Remind staff members of security best practices, including simple steps like locking devices when not in use. Locking devices ensures that unauthorised people cannot access information and tools that should not be available to them.
Cyber security training
One of the best ways to help employees is to have them undertake regular cyber security training. The training material should educate your team on the most common security threats and how they can do their part to reduce the risk of security breaches. In addition, this training should include an email phishing simulation to assess employees’ awareness of, and response to potentially malicious links and files. Simulation outcomes will give the leadership team guidance on areas that need to be a focus for the business.
Sign up for a dark web, phishing simulation and security awareness bundle with New Era
New Era Technology’s bundle of security services provides organisations with three core services to protect against user-targeted IT security threats. Notably, businesses that undertake these services will be developing a security-focused culture where employees are empowered to take responsibility for their role in security. Security training and exercises will increase the chance of identifying and reducing the impact of data breaches, protecting assets and data and preventing potential downtime.
Undertaking exercises like this will also help businesses stay compliant with a range of requirements, including cyber insurance applications and security processes and frameworks.

 Canada
Canada LATAM
LATAM New Zealand
New Zealand UAE
UAE United Kingdom
United Kingdom United States
United States