Firewall technology has been the cornerstone of network and security team efforts globally since the early 1990s. The first generation of this technology was straightforward and focused on source IP, destination IP, port, and protocol. However, this required an engineer to build both inbound and outbound rule sets as the firewall was unaware of the “state” of the connection. The second-generation (circuit firewalls) added the intelligence to monitor the “state” of a connection; thus, an engineer was only required to build one set of rules that applied to the connection bi-directionally.
The third generation of firewall technology added intelligence to understand how various protocols work and adapt to their use in real-time. This change was the beginning of the functionality in Next-Generation Firewalls (NGFW) that are in use today.
The NGFW of modern times is capable of far more than first-generation firewalls of times past. However, many networking teams are still using this modern technology the same way as the previous versions. Therefore, this article will focus on ways to better utilize your NGFW.
Intrusion Detection and Prevention on NGFW
Intrusion Detection (IDS) and Prevention (IPS) systems have been integrated directly with NGFWs for threat detection and prevention on packets traversing the firewall. Most companies have deployed this technology at the edge of their networks, but the same mechanism can be deployed to detect threats originating within the Local Area Network (LAN). For example, consider the following two scenarios:
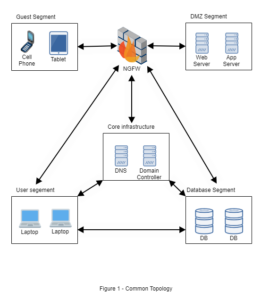 | 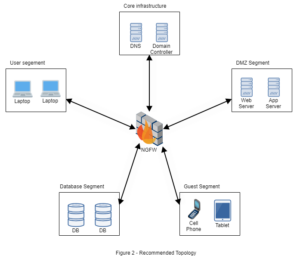 |
| Figure 1 represents common deployments of firewalls, but it does not allow the NGFW to inspect the traffic going between LAN segments. Threats that originate within the LAN would not be blocked or alerted upon. | In Figure 2, the NGFW now inspects all packets flowing between network segments, applies traditional firewall rule sets, and performs deep packet inspection for threat detection and prevention. |
Web Content Filtering
As part of a layered security strategy, filtering Internet-based content that user endpoints can access is crucial, protecting them from threats such as phishing, malvertising, zero-day malware, advanced persistent threats, and more. As a byproduct of protecting endpoints and users, Web Content Filtering protects the enterprise’s data and brand by minimizing the risk associated with these web-based threat vectors. You may ask, “How does this apply to an NGFW?” NGFWs now have this intelligence baked into the appliance. It allows for full web content filtering at the network layer, allowing policies to be applied to IoT, printers, guest networks, and other segments where host-based controls cannot be installed on the endpoint. This capability is where the NGFW web content filtering shines and is an example of how NGFWs fit into a security program’s strategy for data center security.
Data Loss Prevention
Traditional Data Loss Prevention (DLP) technology uses agents, gateways, scanners, and other methods to find and protect a company’s sensitive data. However, often there is hesitation in putting a DLP gateway in line with the egress point(s) of a network due to introducing a single point of failure. IT teams understandably want to minimize downtime as much as possible.
NGFW’s now have DLP functionality as an add-on to the existing firewall, relieving organizations of another inline appliance that may cause network downtimes, congestion, or other operational issues. Additionally, implementing this module on an edge NGFW is a quick win for teams concerned with sensitive data leaving their networks.
Threat Intelligence Feeds
Attackers are constantly changing their tools and techniques (TTs) used to target organizations. Due to these challenges, the way we look at threat intelligence has shifted from manual review to automation by integrating intelligence feeds directly with firewalls. By automating this integration, rules that block known attacker infrastructure can move away from static, rarely updated rule sets to a more dynamic state that can keep pace with the enemy’s velocity. These feeds can even be configured to leverage intelligence from other security technologies deployed within your environment with relative ease.
Advanced Firewall Rule Sets
Instead of building traditional firewall rules with IPs, ports, and protocols, these same rules can be implemented using applications and Identity Provider attributes such as username or group membership.
NGFWs come with the functionality that allows organizations to deploy firewall rules that target specific applications through behavioral characteristics and implement Role-Based Access Controls (RBAC) at the network layer. This is a huge step forward for enforcing RBAC throughout the network.
Summary
In summary, NGFWs pack a serious punch. They are far more capable of introducing advanced protection mechanisms at the edge or within the LAN with the correct topology than previous generations of firewalls. Furthermore, by leveraging capabilities of the NGFW, technical debt incurred from the deployment of multiple disconnected security systems can efficiently be aggregated in a single platform, leading to improvements in an organization’s security posture, reducing administrative burden and complexity, and allowing for a greater Return on Investment (ROI).
New Era Technology Can Help
New Era Managed Detection & Response (MDR) service can assist you with implementing Next-Generation Firewalls, as well as firewall log aggregation, monitoring, and response. If you are interested in learning more about how your organization can prevent, detect, and maintain threats through New Era MDR, please visit our page or email us at solutions@neweratech.com to get started.

 Canada
Canada Australia
Australia New Zealand
New Zealand UAE
UAE United Kingdom
United Kingdom




